Critical Changes to UK Cyber Security Rules Under the Cyber Security and Resilience Bill


As cyber threats evolve from simple disruptions to sophisticated attacks capable of threatening national security, the existing legal frameworks are straining to keep pace. In response, the UK Government has introduced the Cyber Security and Resilience Bill, a landmark piece of legislation set to fundamentally reshape how the nation’s most vital services and their digital supply chains protect themselves. This Bill is not merely an update; it represents a new era of accountability, demanding a strategic shift from baseline compliance to proactive, demonstrable resilience.
The Shifting Threat Landscape and Legislative Imperative
The original Network and Information Systems (NIS) Regulations of 2018 were a crucial first step in securing the UK's essential services. However, the nature of cyber threats has transformed dramatically. State-sponsored actors, ransomware gangs, and other malicious groups now frequently target the sprawling digital supply chains that underpin critical sectors like energy, transport, and water. An attack on a single software provider or a managed service provider can have a cascading effect, disrupting multiple essential services simultaneously. The UK Government has recognised that the old rules, which focused primarily on the frontline operators, no longer provide sufficient protection against these modern, systemic risks.
Why This Bill Matters to Every Organisation
The Cyber Security and Resilience Bill extends its reach far beyond the traditional operators of essential services. It brings critical third-party suppliers, particularly managed service providers (MSPs) and data centres, directly into the regulatory fold. This means that any organisation providing digital services to the UK's critical infrastructure will now face new, stringent security and reporting obligations. The legislation codifies a new reality: cybersecurity is a shared responsibility, and weakness anywhere in the supply chain is a threat to national security. Ignoring these changes is not an option, as the Bill introduces significant penalties for non-compliance.
Understanding the Cyber Security and Resilience Bill: A Foundational Shift
To fully grasp the Bill's impact, it's essential to understand its origins and core aims. It builds upon the foundation of the NIS Regulations but significantly expands its scope and deepens its requirements, reflecting lessons learned over the past several years and aligning with international trends in cyber security legislation.
From NIS to Resilience: The Evolution of UK Cyber Law
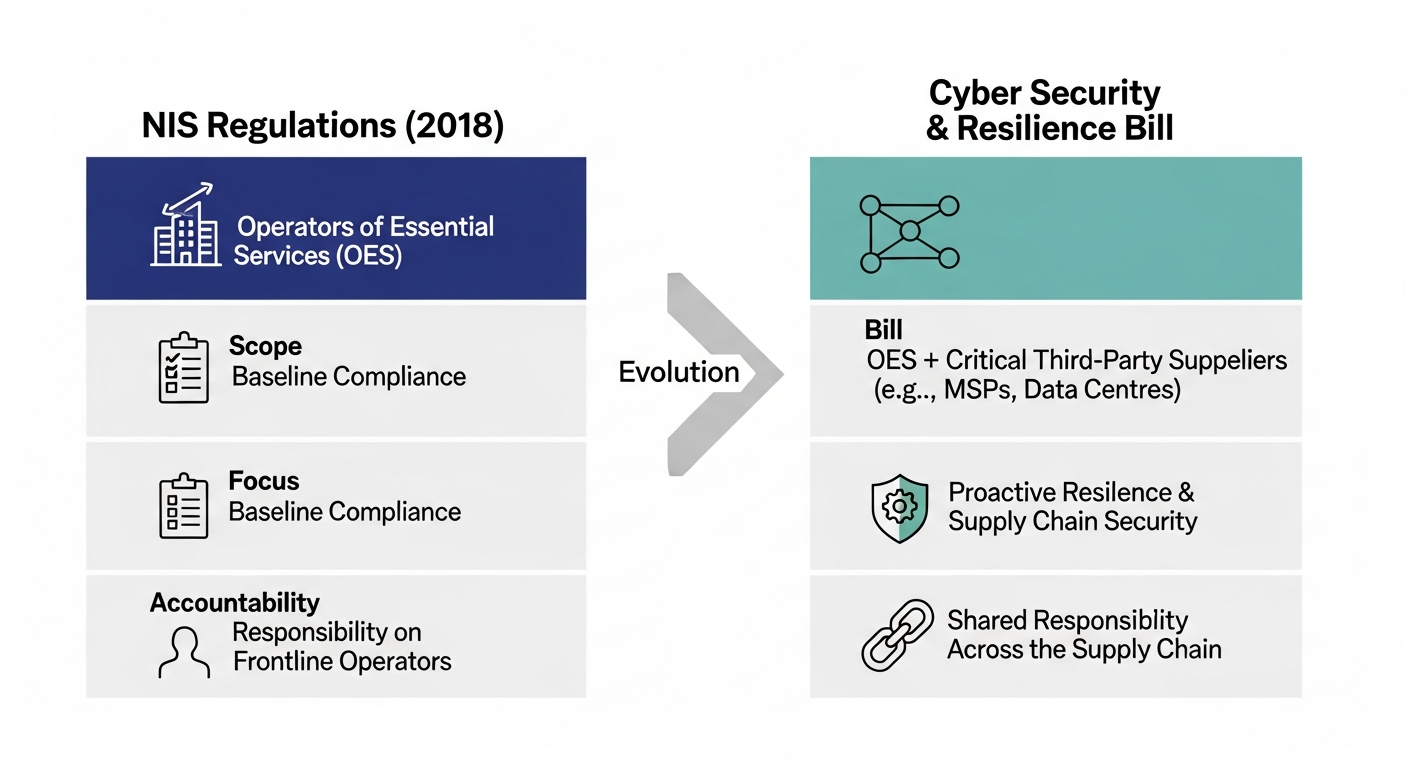
The Cyber Security and Resilience Bill significantly evolves UK cyber law, expanding its scope and shifting its focus from baseline compliance to proactive, supply-chain-wide resilience.
Core Objectives: What the Bill Aims to Achieve
The UK Government has outlined several clear objectives for the Cyber Security and Resilience Bill. At its core, the legislation aims to:
- Protect Essential Services: Strengthen the security and resilience of services vital to the UK's economy and public safety against disruption from cyber incidents.
- Secure the Supply Chain: Bring critical third-party suppliers, especially managed service providers, under direct regulatory oversight to mitigate systemic risks.
- Modernise Regulations: Update the legal framework to reflect the current technological landscape and the sophisticated nature of modern cyber threats.
- Enhance Incident Reporting: Create a more streamlined and effective system for reporting cyber incidents to ensure a coordinated national response, with the National Cyber Security Centre (NCSC) playing a key role.
- Strengthen Enforcement: Grant regulators the necessary powers and tools to enforce compliance effectively, including the ability to levy substantial fines.
Expanded Scope: Who is Now Under the Spotlight?
One of the most significant changes introduced by the Bill is the dramatic expansion of its regulatory scope. It moves beyond the original list of operators to encompass the wider ecosystem that supports them, ensuring accountability is distributed throughout the digital supply chain.
Operators of Essential Services (OES) and Relevant Digital Service Providers (RDSPs)
Organisations already designated as OES in sectors like energy, transport, water, and healthcare, along with RDSPs such as online marketplaces and search engines, will remain under regulation. However, they will face updated and more rigorous requirements. The Bill empowers the government to amend the details of the NIS Regulations more easily, allowing it to adapt to new threats and technologies without needing primary legislation. This means existing OES and RDSPs must prepare for a more dynamic and demanding regulatory environment.
Bringing New Entities into the Fold: Critical Suppliers and Managed Service Providers (MSPs)
The Bill's most impactful change is the creation of a new category for "critical suppliers" of services to OES and RDSPs. This primarily targets managed service providers, which offer services like security monitoring, IT outsourcing, and managed network services. By gaining access to their clients' networks and data, MSPs can become a single point of failure. A compromise of one MSP could grant an attacker access to dozens of critical organisations. Under the new rules, the government can designate specific MSPs and other critical suppliers, subjecting them to the same robust security duties and incident reporting mandates as the essential services they support.
The End of Automatic Exemptions for SMEs?
Previously, certain digital services providers were exempt from NIS regulations based on their size (fewer than 50 staff and under €10 million annual turnover). The Resilience Bill proposes removing this automatic exemption. While proportionality will still be a factor, the government will have the power to bring smaller but systemically important companies into scope. This acknowledges that a small, specialised software provider could be a critical link in the supply chain for a major national infrastructure operator, making its security a matter of national interest regardless of its size.
Enhanced Security Requirements: Raising the Bar for All
The Bill doesn't just expand who is regulated; it raises the standard of what is required. It pushes organisations beyond a compliance-focused checklist towards a more holistic and proactive approach to managing cyber risk, with a strong emphasis on operational resilience.
Proactive Risk Management and Cyber Governance
Organisations will be expected to treat cyber security as a core governance issue, not just an IT problem. This involves establishing clear lines of accountability, conducting comprehensive and regular risk assessments, and ensuring that senior leadership is actively engaged in cyber risk management. The focus is on embedding security into organisational culture and decision-making processes, ensuring risks are understood and managed from the top down.
Specific Technical and Organisational Measures
While the Bill sets out high-level principles, regulators will be empowered to provide more specific guidance on required measures. These will likely align with frameworks from the National Cyber Security Centre (NCSC) and cover areas such as access control, encryption, network security, vulnerability management, and staff training. The expectation is that organisations will implement robust, multi-layered defences tailored to their specific risk profile.
Focus on Resilience Beyond Just Prevention
The legislation explicitly incorporates the concept of "resilience." This acknowledges that not all cyber incidents can be prevented. Therefore, organisations must not only have strong defences but also robust plans to withstand, respond to, and recover from an attack. This includes developing and regularly testing incident response plans, maintaining backups, and ensuring business continuity strategies are in place to minimise disruption to essential services during and after a cyber incident.
Incident Reporting: Faster, Broader, More Accountable
Effective incident response relies on timely and accurate information. The Bill aims to strengthen and streamline the UK's incident reporting framework to provide regulators and the NCSC with the visibility needed to manage national-level cyber events.
Streamlined and Strengthened Incident Reporting Obligations
The new rules will require all regulated entities, including newly designated critical suppliers, to report significant cyber incidents to their relevant regulator without undue delay. The Bill also introduces the power to mandate reporting of other types of cyber incidents, or even potential threats, that may not meet the "significant" threshold but could still provide valuable intelligence. The goal is to build a more comprehensive picture of the threat landscape facing the UK.
The Central Role of the National Cyber Security Centre (NCSC)
The NCSC will continue to be the UK's technical authority on cybersecurity and will play a pivotal role under the new regime. It will support regulators by providing expert guidance, analysing incident data to identify national trends, and coordinating the response to major cyber incidents that affect national security. The Bill formalises the NCSC's role as the central hub for cybersecurity information and response coordination.
Enforcement and Penalties: Real Consequences for Non-Compliance
To ensure the new rules have the desired effect, the Bill grants regulators significantly enhanced enforcement powers and introduces stringent penalties for failures in compliance.
Increased Regulatory Powers and Scrutiny
Competent authorities and regulators will have broader powers to investigate incidents and assess the cyber security measures of regulated entities. This can include conducting audits, compelling the provision of information, and issuing legally binding instructions to improve security practices. Organisations should anticipate a higher level of regulatory scrutiny and be prepared to demonstrate their compliance proactively.
Significant Financial Penalties
The Bill maintains the two-tiered penalty system but ensures it applies across the newly expanded scope. For the most severe contraventions, such as a failure that leads to a significant disruption of an essential service, fines can reach up to £17 million or 4% of an organisation's global turnover, whichever is greater. This aligns with the penalty levels seen in other major UK regulations like GDPR and underscores the government's serious commitment to enforcement.
Reputational Damage and Operational Disruptions
Beyond financial penalties, non-compliance carries significant risks of reputational damage and operational disruption. A major cyber incident resulting from inadequate security can destroy public trust, damage customer relationships, and lead to prolonged service outages. The cost of remediation and recovery often far exceeds the initial regulatory fine, making investment in resilience a critical business imperative.
Practical Steps for Compliance: Building a Resilient Future
Navigating these critical changes requires proactive preparation. Organisations should not wait for the Bill to become law to begin assessing their posture and planning for compliance.
Comprehensive Risk Assessment and Gap Analysis
The first step is to understand your organisation's position. Conduct a thorough risk assessment to identify your most critical assets and services. Perform a gap analysis comparing your current security controls and policies against the likely requirements of the new Bill and guidance from the NCSC.
Strengthening Your Supply Chain Security Program
Evaluate your entire digital supply chain. Identify all third-party suppliers, particularly MSPs, that have access to your networks or data. Review contracts to ensure they include clear cybersecurity requirements and begin assessing the security posture of your most critical suppliers.
Enhancing Incident Response and Recovery Capabilities
Review and update your incident response plan to align with the new, faster reporting timelines. Conduct regular drills and tabletop exercises to test your ability to detect, respond to, and recover from a major cyber incident. Ensure your recovery plans are robust and tested.
Investing in Technology and Training
Invest in the right technology to defend against modern cyber threats and provide visibility across your network and supply chain. Equally important is investing in your people. Foster a strong security culture through continuous training and awareness programs for all employees, from the boardroom to the front line.
Engaging with Regulators and Industry Best Practices
Stay informed about the Bill's progress and the subsequent guidance issued by regulators and the NCSC. Engage with industry bodies and peer groups to share best practices for building resilience. A collaborative approach will be key to successfully navigating this new regulatory landscape.
Conclusion
The Cyber Security and Resilience Bill is a clear signal from the UK Government that the bar for cyber security is being raised for everyone involved in delivering the nation’s essential services. By expanding its scope to include critical suppliers and managed service providers, focusing intently on the security of supply chains, and mandating a shift towards genuine operational resilience, the legislation addresses the systemic risks of our hyper-connected world.
For organisations, the message is unequivocal: cyber security is no longer a peripheral IT function but a core component of corporate governance and national security. The potential for £17 million fines provides a compelling incentive, but the true driver for change should be the strategic advantage that comes with being a resilient, secure, and trustworthy organisation. The time to prepare is now. By undertaking comprehensive risk assessments, securing supply chains, and embedding a culture of resilience, businesses can not only ensure compliance but also build a stronger, safer digital future for the UK.
Incident Response is a critical pillar of the Cyber Security and Resilience Bill.
Make sure your organisation is ready.
Explore our full range of services from tabletop exercises to incident response retainers and give your business the capability and confidence to withstand a cyber attack, and crucially, demonstrate resilience when it matters most.
.png)








.svg)








.webp)


