Your Definitive Guide to Crafting a Resilient 2026 Cyber Strategy


Introduction: Why 2026 Demands a Resilient Cyber Strategy
As we look toward 2026, the digital frontier is no longer a landscape of distant threats but an immediate, dynamic environment where resilience is the ultimate currency. The frequency and sophistication of cyber threats are accelerating, fueled by geopolitical tensions, technological advancements, and interconnected global economies.
The Shifting Paradigm: From Prevention to Enduring Resilience
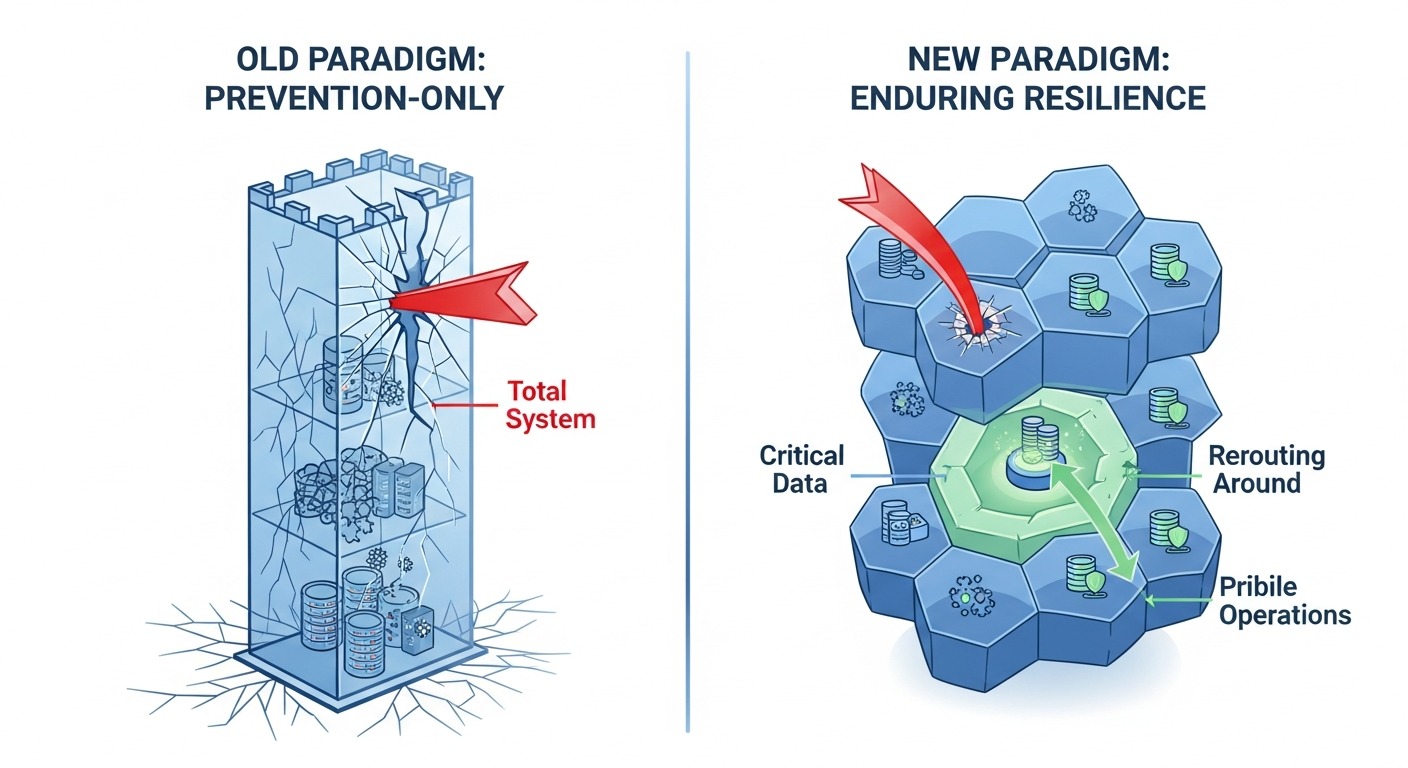
The strategic shift from a fragile 'prevention' model to a durable 'resilience' model that can absorb, adapt to, and recover from attacks.
Navigating the 2026 Threat Landscape: Key Dangers and Disruptors
Understanding the terrain is the first step in building a formidable defense. The 2026 threat landscape is not merely an evolution of today's challenges; it represents a fundamental shift in how attackers operate and what they target. A resilient strategy must be grounded in a clear-eyed assessment of these emerging dangers.
The AI Arms Race: Attackers' New Playbook
Artificial intelligence has democratized cybercrime. Threat actors are now leveraging AI to generate highly convincing phishing emails at scale, create polymorphic malware that evades signature-based detection, and automate reconnaissance to find vulnerabilities faster than any human team. This AI-powered offense means defenders must counter with AI-driven defenses, using machine learning to detect anomalies and predict attacker behavior before it results in a breach.
Evolving Ransomware and the Shift to Data Exfiltration
Ransomware is no longer just about encryption. Modern attackers now prioritize data exfiltration, creating a double extortion scenario: pay to decrypt your files and pay again to prevent the public release of your sensitive data. This tactic dramatically increases pressure on victims and complicates incident response. For industries like healthcare, where the average cost of a data breach has soared to $9.77 million, the consequences of such breaches are financially crippling.
Building the Core: Foundational Pillars of a Resilient Strategy
With a clear view of the threat landscape, the next step is to construct the foundational pillars of resilience. These principles are not about specific tools but about a strategic architectural approach that reduces the attack surface, limits the blast radius of an incident, and ensures the integrity of your core assets.
Strategic Continuous Exposure Management (CEM)
You cannot protect what you cannot see. Continuous Exposure Management (CEM) is an integrated approach that provides a holistic, attacker's-eye view of your organisation's exposures. It moves beyond traditional vulnerability scanning by consolidating asset discovery, vulnerability assessment, and threat intelligence to prioritize the risks that matter most. A successful CEM program enables organisations to proactively identify and remediate potential attack paths before threat actors can exploit them.
Holistic Cloud Security Posture Management
Securing the cloud requires a dedicated, holistic approach. Cloud Security Posture Management (CSPM) tools automate the identification of misconfigurations and compliance risks across multi-cloud environments. However, a resilient strategy integrates CSPM with other security functions, such as identity and access management and data protection. This ensures that cloud security is not a siloed process but an integral part of the overall cyber security posture, protecting against common vulnerabilities that lead to breaches.
Data Integrity and Resilience
At the heart of any resilience strategy is the data itself. Beyond simple backups, data resilience involves ensuring data is accurate, available, and tamper-proof. This means implementing immutable storage for critical backups to protect them from ransomware, employing strong encryption for data at rest and in transit, and having well-rehearsed processes for rapid data recovery. The goal is to ensure that even if systems are compromised, your core data remains intact and recoverable.
Strategic Technology Integration: Empowering Defenders in 2026
Foundational principles must be supported by the right technology. The key to a resilient 2026 strategy is not simply acquiring more tools but strategically integrating advanced technology to create a cohesive, intelligent, and automated defense system that empowers human security teams.
AI for Defense: Enhancing Detection, Response, and Prediction
Just as attackers use AI for offense, defenders must leverage it for defense. AI and machine learning algorithms can analyze vast amounts of security data in real-time to identify subtle patterns and anomalies indicative of a cyber threat. This technology enhances Security Operations Centers (SOCs) by automating threat detection, prioritizing alerts to reduce analyst fatigue, and even predicting potential future attacks based on emerging trends and threat intelligence.
Layered Defenses and Microsegmentation for Containment
Assuming a breach will eventually occur, the focus shifts to containment. Microsegmentation is a powerful technology that divides a network into small, isolated zones, preventing attackers from moving laterally from a compromised system to other parts of the environment. By creating granular security policies for each segment, you can ensure that even if one workload is breached, the damage is contained, minimizing the overall impact on business operations.
Preparing for the Quantum Era: Crypto-Agility for 2026 and Beyond
While the full impact of quantum computing may be years away, its ability to break current encryption standards requires proactive preparation. A resilient 2026 strategy must incorporate the concept of crypto-agility—the ability to seamlessly transition to new, quantum-resistant cryptographic algorithms as they become available. This involves identifying critical data and systems that rely on legacy encryption and developing a roadmap for upgrading them, ensuring long-term data confidentiality.
The Human Firewall: Cultivating a Resilient Security Culture
Technology and processes are essential, but the most adaptive element of any defense is its people. Shifting the mindset from viewing employees as the "weakest link" to empowering them as the "human firewall" is a critical component of a resilient cyber strategy.
Empowering People as the Strongest Defense
A resilient security culture is built on empowerment, not fear. This involves moving beyond basic annual training to continuous education that is relevant, engaging, and tailored to specific roles. When people understand the "why" behind security policies and are equipped with the knowledge to identify sophisticated social engineering and phishing attempts, they become active participants in the organisation's defense, reporting threats and practicing secure behaviors instinctively.
The Synergy of Human Intuition and AI for Enhanced Security
The future of cyber defense lies in the synergy between human expertise and machine intelligence. AI can process data at a scale no human can match, but human analysts provide the critical context, intuition, and creative problem-solving skills needed to investigate complex threats. With an estimated 3.5 million unfilled cyber security positions expected globally in 2026, optimising this partnership is crucial. Automation handles the repetitive tasks, freeing up human talent to focus on strategic threat hunting and incident response.
Operationalising Resilience: Frameworks, Governance, and Continuous Improvement
A truly resilient cyber strategy is not a one-time project but a continuous, living program integrated into the fabric of the business. This requires robust operational frameworks, clear governance, and a commitment to perpetual improvement.
Integrating Cyber Strategy with Business Continuity
Cyber security can no longer be separate from business continuity and disaster recovery planning. A resilient organisation aligns these functions, ensuring that incident response plans are designed not just to stop an attack but to restore critical business processes within predefined tolerance levels. This integration requires collaboration between IT, security, and business leaders to identify essential services and dependencies.
Establishing a Robust Incident Response and Recovery Plan
A well-documented and frequently tested incident response (IR) plan is the cornerstone of operational resilience. This plan should detail every step, from initial detection and containment to eradication and recovery. It must define communication protocols for stakeholders, legal counsel, and regulatory bodies. Regular drills and tabletop exercises ensure the IR team is prepared to act decisively and efficiently when a real incident occurs.
Conclusion: Your Resilient Future in 2026 and Beyond
Crafting a resilient cyber strategy for 2026 is an exercise in foresight, integration, and continuous adaptation. It requires moving beyond outdated models of perimeter defense toward a dynamic, identity-centric approach that anticipates and withstands modern cyber threats. By focusing on the core pillars of Zero Trust, exposure management, and data integrity, organisations can build a foundation strong enough to weather the inevitable storms.
Recap of Key Strategic Imperatives for a Resilient 2026
The journey to resilience is built on several key imperatives. First, deeply understand the evolving threat landscape, particularly the impact of AI and vulnerabilities in your cloud and supply chains. Second, build your defense around foundational pillars: treat identity as the new perimeter, continuously manage your exposure, and ensure data integrity. Third, strategically integrate technology like AI and microsegmentation not as silver bullets, but as enablers for your human defenders. Finally, operationalize resilience through robust governance, tested response plans, and a security-aware culture.
.png)








.svg)








.webp)


