Essential Security Culture Behaviours for 2026


Essential Security Culture Behaviours for 2026
Why Security Culture is Your Ultimate Defense in 2026
In the dynamic digital landscape of 2026, technology alone is no longer the impenetrable shield it once promised to be. The most sophisticated firewalls and advanced threat detection systems can be rendered obsolete by a single, well-executed human exploit. This reality underscores a critical shift: the paramount importance of security culture.
By 2026, a robust, deeply ingrained security culture is not just a best practice; it is your ultimate defense, a resilient human firewall that adapts, learns, and protects. This guide provides the essential behaviours and strategies needed to build and maintain such a culture, ensuring your organisation is prepared for the evolving threats ahead.
The Shifting Landscape: Beyond Technology to Human Resilience
The traditional cyber security paradigm, heavily reliant on technological defenses, is increasingly proving insufficient. As threats become more sophisticated, they increasingly target the human element within organisations. This evolution necessitates a fundamental re-evaluation of our approach, moving beyond mere technical controls to foster genuine human resilience. The focus must shift from simply preventing breaches to empowering every employee to be an active participant in the organisation's security. In 2026, the most significant vulnerabilities are not found in code, but in human behavior, perception, and decision-making.
The Evolving Threat Landscape & Magnified Human Vulnerabilities in 2026
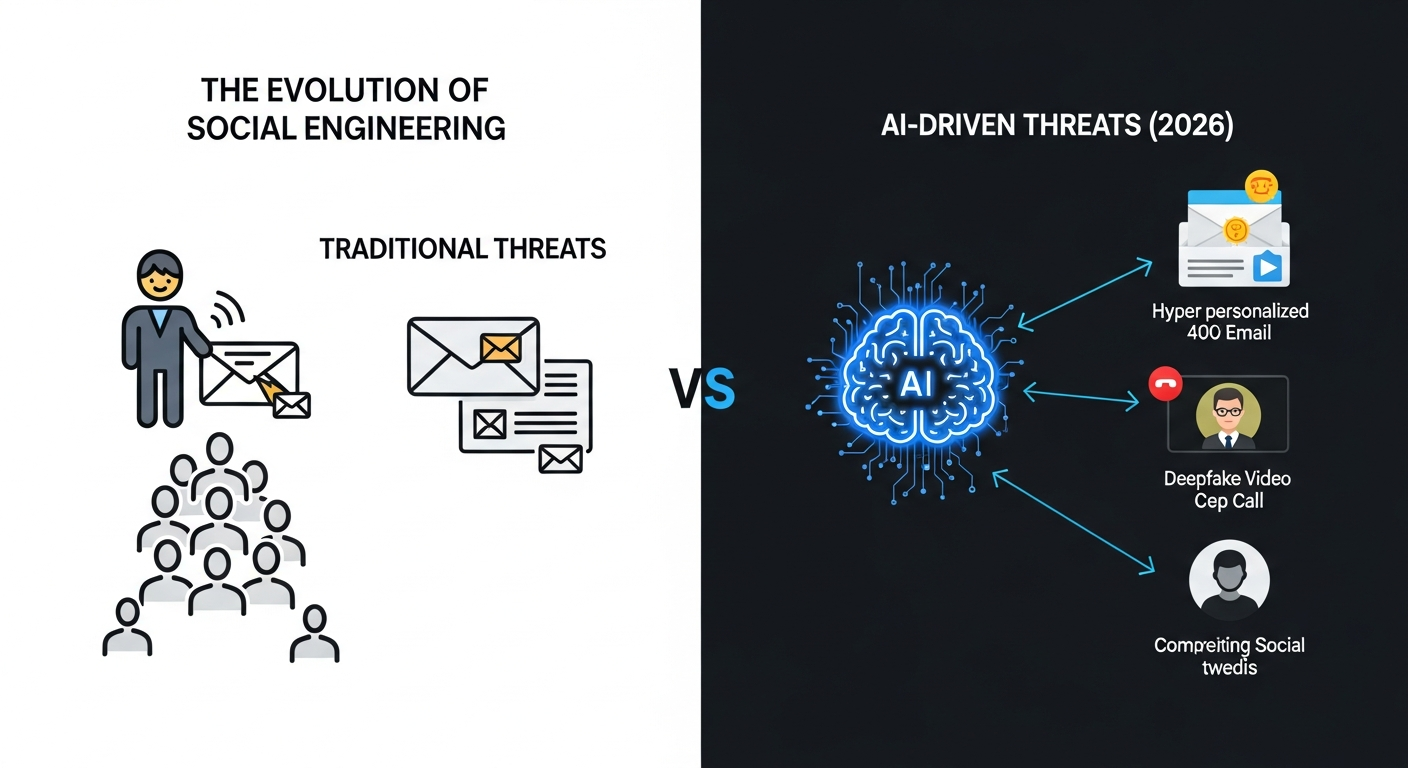
AI-Driven Threats: The New Frontier of Social Engineering
Artificial intelligence is rapidly transforming the threat landscape, particularly in the realm of social engineering. Sophisticated AI tools can now generate hyper-personalised phishing emails, deepfake voice and video messages, and convincingly crafted social media profiles. These AI-generated phishing emails have more than four times the click rate of human-written ones (54% vs. 12%) Hunto AI, 2026. This dramatically increases the likelihood of employees falling victim to scams, mistaking malicious content for legitimate communications. The ability of AI to mimic human interaction so convincingly requires a new level of employee vigilance and critical thinking.
The Expanding Attack Surface: Remote Work, BYOD, and Cloud
The persistent rise of remote and hybrid work models, coupled with the widespread adoption of Bring Your Own Device (BYOD) policies and an increased reliance on cloud services, has dramatically expanded the traditional network perimeter. In 2025, 78% of organisations reported at least one security incident linked to remote work, with the average cost of a remote work-related breach rising to $4.56 million ElectroIQ, 2025. Phishing remains the most frequent attack type in these environments, accounting for 43% of initial breach attempts in 2025 ElectroIQ, 2026. This decentralisation introduces a myriad of new entry points for attackers, placing greater responsibility on individual employees to secure their devices and environments.
Persistent Human Factors: Insider Threats and Cognitive Biases
Beyond external threats, internal factors continue to pose significant risks. Insider threats, whether malicious, negligent, or compromised, remain a potent danger. The global average cost resulting from insider threats reached $15.38 million in 2025, underscoring the severe financial implications IBM, Varonis, 2025. Compounding this is the inherent nature of cognitive biases. Humans are prone to confirmation bias, availability heuristic, and other psychological shortcuts that adversaries expertly exploit. In 2024, 68% of security breaches involved the human element Verizon DBIR, Infrascale, TechRadar 2025, highlighting the persistent need to address these underlying human tendencies.
Building a High Trust, Security First Organisational Culture
Cultivating a robust security culture begins with establishing a foundational environment of trust and shared responsibility. This is not solely the domain of the IT department; it requires intentional effort from leadership and management to embed security into the very fabric of the organisational culture.
Leadership at the Forefront: Setting the Tone for Security
Leadership plays a pivotal role in shaping any organisational culture, and security is no exception. When leaders visibly prioritise and champion security, it sends a clear message throughout the organisation. This involves not just verbal endorsement but tangible actions: allocating adequate resources, integrating security into strategic decision-making, and holding themselves and their teams accountable. Leadership’s commitment demonstrates that security is a core business enabler, not just a compliance checkbox. This commitment is essential for driving genuine employee engagement with security initiatives.
Fostering a Just and Reporting Culture
A fundamental aspect of a healthy security culture is the establishment of a "just culture." This means creating an environment where employees feel safe to report security concerns, near misses, or even mistakes without fear of undue punishment. When employees understand that reporting is valued and leads to learning and improvement, rather than blame, they are more likely to come forward. This transparency is vital for identifying emerging threats and weaknesses before they escalate into major security incidents. A just culture directly supports a proactive approach to security, turning potential weaknesses into opportunities for growth.
Integrating Security into Core Values and Everyday Operations
For security to become truly embedded, it must move beyond being a separate initiative and be integrated into the organisation's core values and daily operations. This means security considerations should be part of project planning, product development, and employee onboarding. When security is a natural part of how work gets done, rather than an afterthought, it becomes an instinctive practice. This integration reinforces the idea that every employee, regardless of their role, contributes to the organisation's overall security posture.
Pillars of Resilience
With a strong cultural foundation in place, we can define the specific behaviors that empower individuals and fortify the organisation against modern threats. These behaviors act as the pillars of resilience, essential for navigating the complexities of 2026.
Proactive Threat Detection and Reporting
Every employee can act as a vital sensor within the organisation's security network. This involves developing a keen awareness of potential threats, such as unusual email content, unexpected requests, or suspicious system behavior, and knowing how to report them promptly. This proactive stance, coupled with a clear reporting mechanism, is crucial for early detection. It’s estimated that nearly 1.2% of all emails sent are malicious, accounting for 3.4 billion phishing emails daily Keepnet Labs, Hunto AI, 2026, making each employee’s vigilance indispensable.
Smart Authentication & Access Management
Moving beyond simple password practices, employees must adopt smarter authentication methods. This includes utilising multi-factor authentication (MFA) consistently, practicing strong password hygiene where MFA is not universally applied, and understanding the principle of least privilege. Secure access management is critical, as 83% of breaches involve stolen credentials IBM, Varonis, 2025. Employees must be vigilant about safeguarding their credentials and understanding when and how to grant access.
Secure Data Handling and Privacy Practices
Understanding the sensitivity of data and adhering to strict data protection protocols is paramount. This involves recognising different data classifications, knowing where and how sensitive information can be stored and shared, and understanding privacy regulations. Employees must be mindful of their data handling practices, especially in remote environments where data might be accessed on less secure networks or devices. This behaviour directly contributes to preventing data breaches, the global average cost of which was $4.44 million in 2025 IBM, Varonis, 2025.
Device and Endpoint Vigilance
In an era of BYOD and remote work, employees are responsible for the security of their devices, which often serve as gateways into the corporate network. This behavior includes keeping operating systems and applications updated, using reputable antivirus software, securing Wi-Fi connections, and locking devices when unattended. Endpoint vigilance is a collective responsibility, as compromised devices can lead to widespread security incidents, with endpoint attacks surging over 200% Forrester, IBM, Varonis, 2025.
Critical Thinking and Verification in the AI Age
With the rise of AI-generated content, a critical thinking mindset is no longer optional. Employees must develop the habit of questioning and verifying information, especially communications that seem unusual or urgent. This involves cross-referencing information, being skeptical of unsolicited requests, and utilising established channels for verification. The ability to discern authentic communication from AI-driven deception is a crucial behavior for future security.
Activating Change: Applying Behavioral Science to Security Culture
Simply communicating security best practices is insufficient; true behavior change requires a strategic, science-backed approach. Behavioral science offers powerful insights into how individuals form habits and make decisions, providing effective methods for embedding security into daily routines.
Understanding Attitudes and Behavior Change (ABC Model)
The Attitudes, Behavior, Consequences (ABC) model provides a framework for understanding and influencing behavior. Security awareness training should not only inform employees about threats but also aim to shape their positive attitudes toward security practices. By emphasizing the capabilities required for secure behavior and highlighting the positive consequences of adherence (e.g., preventing breaches, protecting the organisation), we can create a more effective environment for behavior change. Many organisations express concern, as 67% of organisations are concerned that employees lack basic security awareness Fortinet, Keepnet Labs, 2024.
Nudging Towards Security: Design for Desired Behavior
Nudge theory suggests that small, subtle changes in the environment or decision-making process can guide individuals towards desired behaviors without restricting choice. For security, this could involve making secure options the easiest options. Examples include default security settings, prominent reporting buttons, or simplified authentication flows. By making secure behavior frictionless, organisations can increase adoption rates and foster unconscious adherence to security protocols.
Gamification and Positive Reinforcement
Gamification, the application of game-like elements such as points, badges, and leaderboards, can make security training and compliance more engaging. Coupling this with positive reinforcement acknowledging and rewarding secure behaviors can significantly boost employee motivation and participation. Celebrating successful threat reporting or high engagement in security initiatives reinforces positive actions and encourages continued adherence, transforming security from a chore into a shared accomplishment.
Empowering Through Future-Ready Training & Continuous Awareness
The effectiveness of security culture hinges on continuous education and ongoing reinforcement. Training programs must evolve to meet the demands of the 2026 threat landscape, moving beyond annual compliance exercises to become dynamic, engaging, and deeply relevant.
Beyond Compliance: Strategic Security Awareness Training for 2026
By 2026, security awareness training must be strategically designed to address the evolving threat landscape, particularly AI-driven attacks and the expanded attack surface. It needs to move beyond generic "dos and don'ts" to focus on developing critical thinking, threat recognition, and secure decision-making skills. Training should be tailored to specific roles and risk profiles within the organisation, making it more impactful. Only 7.5% of organisations report having adaptive training programs based on regular security awareness test results Keepnet Labs, 2026, highlighting a significant opportunity for improvement in creating more responsive and effective training.
Continuous Learning and "Security Moments"
Security awareness should not be confined to formal training sessions. The concept of "security moments" brief, timely reminders or discussions about security best practices integrated into regular team meetings or daily workflows can be highly effective. This continuous reinforcement keeps security top-of-mind and helps embed secure habits through frequent repetition. These micro-learning opportunities ensure that security remains relevant and actionable in employees' day-to-day tasks.
Leveraging Technology for Smarter Training and Feedback
Technology offers powerful tools for enhancing security training and providing personalized feedback. Phishing simulations, when realistic and contextually relevant, offer invaluable practical experience. AI can also be used to personalise training modules, identify individual learning gaps, and provide immediate, constructive feedback. Leveraging these technologies ensures that training is not only more engaging but also more effective in driving lasting behavior change.
Measuring Success & Cultivating Continuous Improvement
To ensure the efficacy of security culture initiatives, consistent measurement and a commitment to continuous improvement are essential. Understanding what works, what doesn't, and where to adapt is key to maintaining a resilient security posture.
Assessing Your Security Culture Maturity for 2026
Evaluating an organisation's security culture maturity involves looking beyond simple compliance metrics. It requires assessing employee attitudes, observed behaviors, and the overall perception of security within the organisation. Tools and frameworks exist to benchmark current maturity levels, identify areas for improvement, and track progress over time. This assessment should consider the unique challenges and opportunities presented by the 2026 threat landscape.
Data Driven Insights for Optimisation
Metrics are crucial for demonstrating the value of security culture initiatives and for guiding future efforts. This includes tracking the reduction in security incidents, the improvement in reporting rates, the results of phishing simulations, and employee feedback on training programs. By analysing this data, security leaders can gain actionable insights to optimise their strategies, allocate resources effectively, and make informed decisions about future investments in cyber security. Global spending on cyber security products and services is projected to exceed $520 billion annually by 2026 Cyber security Ventures, 2025, emphasising the importance of ensuring these investments yield tangible results through culture.
Adapting to an Ever Changing Landscape
The threat landscape is not static, and neither should be an organisation's approach to security culture. Continuous monitoring of emerging threats, regular review of security policies and training programs, and an agile response to new challenges are vital. By fostering a culture of adaptability and continuous learning, organisations can stay ahead of adversaries and maintain a robust security posture that evolves alongside the risks.
Conclusion
In 2026, the most resilient defense against cyber threats is not built solely on technology, but on the collective strength of a well-cultivated security culture. By prioritising human resilience, fostering a high-trust environment, defining essential behaviors, and leveraging the power of behavioral science and continuous training, organisations can transform their employees into active guardians of their digital assets. This proactive approach, moving beyond mere compliance, is essential for mitigating risks, protecting data, and ultimately, securing a competitive advantage in an increasingly complex digital world. Implementing these strategies requires leadership commitment, management support, and the active engagement of every employee, creating a security-first mindset that permeates the entire organisation.
Frequently Asked Questions (FAQs)
1. What are Essential Security Culture Behaviours?
They are the everyday actions employees take to reduce cyber risk like spotting phishing emails, using MFA, protecting data, and reporting suspicious activity.
2. Why is Security Culture so Important in 2026?
Because attackers target people as much as technology. A strong security culture turns employees into an active line of defence.
3. What Role Does Leadership Play?
Leaders set the tone. When leadership prioritises and models good security practices, the rest of the organisation follows.
4. How Can we Encourage Better Security Behaviour?
Make secure actions easy, provide regular training, reinforce positive behaviour, and create a safe environment for reporting mistakes.
5. How do we Know if our Security Culture is Working?
Look for higher reporting rates, better phishing simulation results, fewer incidents, and stronger employee engagement with security initiatives.
.png)








.svg)








.webp)


