Managed Vulnerability Scanning
Identify and address security weaknesses in your IT infrastructure with Managed Scanning
Enquire.webp)



How Does Managed Vulnerability Scanning Help Your Business Stay Secure?

Reduce Your Window of Risk
While Penetration Testing is a vital part of every businesses cyber security defence procedures, managed vulnerability scanning adds a new layer. Keeping you safe from any emerging vulnerabilities that appear between your manual tests.

Choose When & How Often To Scan
Your business choses when and how often to scan for vulnerabilities. Based on the importance of a particular network or application you can scan daily, monthly, weekly or however you see fit. Giving you control over your companies security footprint.

Comply with Modern Regulations
In most industries that deal with client and sensitive data its mandatory to have regular Penetration Testing carried out on your business. It lets your supply chain and customer base know you’re taking the right steps to securing their information.
Why do You Need
Vulnerability Scanning?
Managed Vulnerability Scanning is an important service for businesses of all sizes. By regularly assessing your organisation’s digital infrastructure for potential weaknesses, you can help protect against cyberattacks and data breaches.
Pentest People’s Managed Vulnerability Scanning Service combines the latest vulnerability scanning tools and experienced security consultants to proactively inspect your network/applications and systems to provide the insight and guidance needed to address security weaknesses.
Our Managed Vulnerability Scanning Service can help businesses save time and resources, while also providing peace of mind that their digital infrastructure is being constantly monitored for potential threats.
Manage Your Vulnerability Scans Directly From SecurePortal
Our Managed Vulnerability Scanning service is accessible through SecurePortal. Allowing you to easily assign scans on any networks/systems or applications. Monitor their discoveries as they happen.Every scan will be reviewed by a Pentest People security consultant, followed by remediation advice for any vulnerabilities discovered.
Managed Vulnerability Scanning
We Now Offer 3 Types of Managed Vulnerability Scanning

Internal Vulnerability Scanning
Protect your organisation from within with our Internal Vulnerability Scanning service.
This service performs a comprehensive security assessment of your internal IT infrastructure. From identifying weak passwords and outdated software to detecting misconfigured settings, we ensure your internal systems are robust and secure. Stay proactive in your defence strategy and safeguard your business against potential insider threats with our advanced scanning technology.

External Vulnerability Scanning
Secure your business with our External Vulnerability Scanning service. We thoroughly examine your external-facing infrastructure to detect and mitigate potential security threats.
Our service identifies vulnerabilities in your network, applications, and systems, offering actionable insights for remediation. Stay ahead of cyber threats and ensure the robustness of your external infrastructure with our advanced scanning technology.

Web Application Vulnerability Scanning
In the digital age, your web applications are key gateways to your business. Our Web App Vulnerability Scanning service provides comprehensive scans to identify potential security flaws within your web apps.
From SQL injection to Cross-Site Scripting (XSS), we detect vulnerabilities and provide actionable insights for remediation. Stay ahead of cyber threats and ensure your web applications are secure and reliable with our cutting-edge scanning technology.
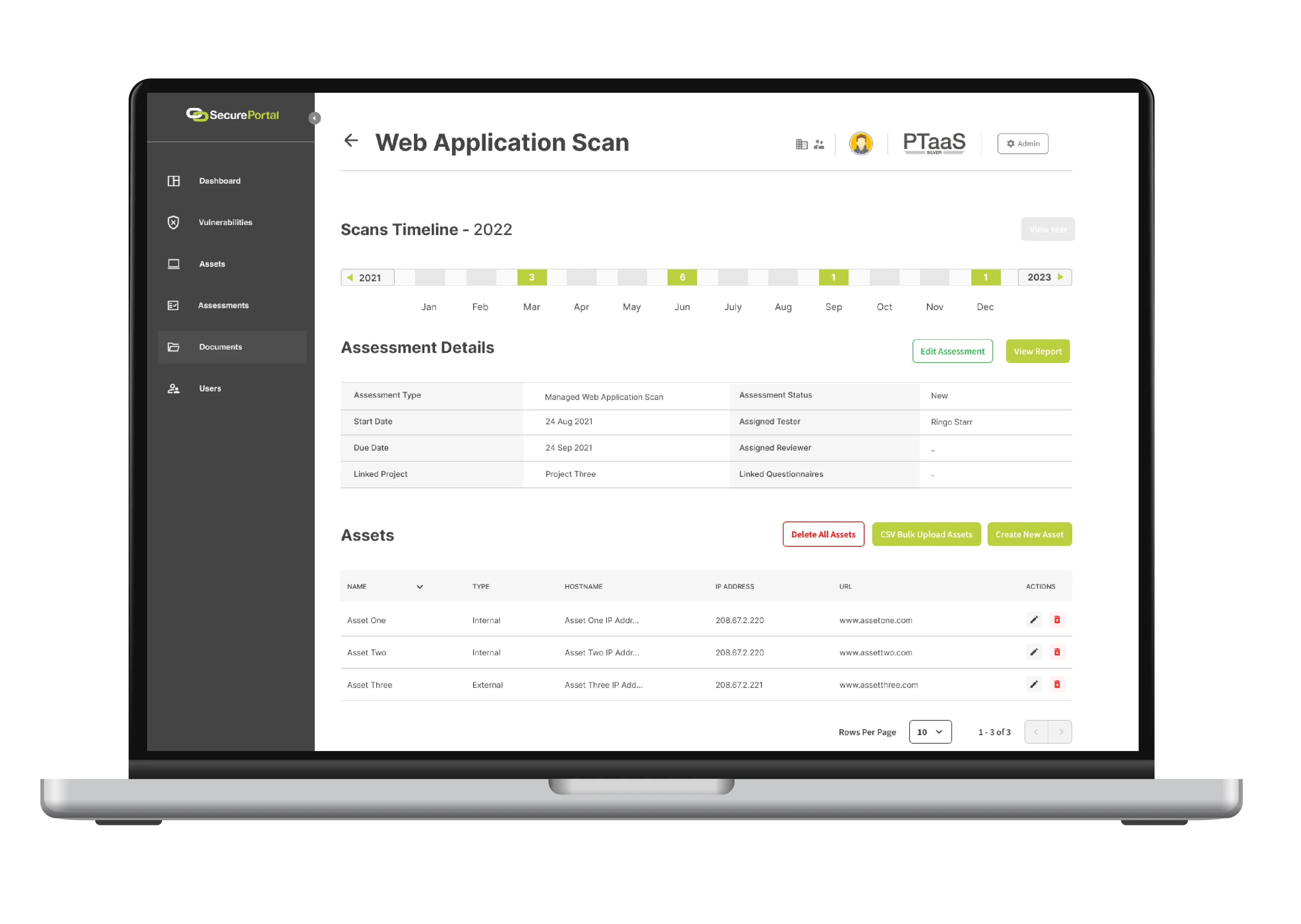
Harness the Power of Vulnerability Scanning Through SecurePortal
Experience efficient and proactive security with our vulnerability scanning feature, integrated directly into our user-friendly SecurePortal platform. This platform provides you with easy access to essential vulnerability data along with valuable remediation advice.
Embrace a proactive and efficient approach to your digital security with SecurePortal's vulnerability scanning feature.

1000’s of Organisations Trust Pentest People For Their Penetration Testing



























Need Any of Our Other Services?
We have an array of Penetration Testing Services to suit all businesses

Infrastructure Penetration Testing
Assess and measure your cyber security through Infrastructure Testing to allow you to manage the identified issues.

Web Application Penetration Testing
Assess your critical Web Applications for Security Vulnerabilities with our Web Application Testing Service.

Social Engineering Assessments
Research, develop and manage an assessment of the security of your people and processes utilising the latest techniques with our social engineering security services..

VPN Configuration Assessments
Assess the VPN security configuration of your network to ensure a misconfiguration or vulnerability is not allowing external access to your corporate network.

Firewall Ruleset Reviews
Assess your Firewall Rule Configuration looking for security issues and unnecessary rules that could lead to a breach of your network with a firewall penetration test.

Network Device Security Reviews
Assess the critical network devices that make up your corporate network looking for software and configuration vulnerabilities.
Experienced Consultant Team
Our Penetration Testing Team are CREST Accredited & Includes CHECK Team Leaders
Experienced & Accredited Testing Team For All Our Services
Penetration testing is a key component of any effective cybersecurity strategy, and it requires well-trained professionals to execute. Our consultant team needs are highly trained in order to test your business for vulnerabilities and identify potential threats before they cause harm. Our team have a deep understanding of the systems and protocols involved in protecting against hackers, malware, and data breaches.
- CHECK Team Leaders
- CREST Accredited consultant teams
- Experts in all areas of cybersecurity



Testimonials
See What Our Clients Have To Say
Pentest People recognise the power of partnerships and are focused and committed to building.









.webp)











.svg)







.webp)

